Hybrid Integrations in Azure
In this article I will shed light on some of the available techniques in implementing Hybrid integration models using Azure along with some context with regards to the organizations decisions within the new integration landscape.
New Integration Landscape
Over the past 7 years or so, Microsoft integration landscape has been evolving going beyond the typical on-premises integration platforms with the paradigm shift introduced by Azure cloud platform and its integration offerings.
Azure integration offerings started with Service Bus, BizTalk Services (now deprecated), all the way to today’s Azure Integration Services – an iPaaS solution suite of services covering APIs, Messaging, Eventing, and Orchestration capabilities.
This new paradigm introduced different integration topologies/models which led organizations to start assessing the potential benefits of leveraging these new models and decide on whether their existing solutions should be moved entirely to the cloud, remain on-premises, or span across the two realms.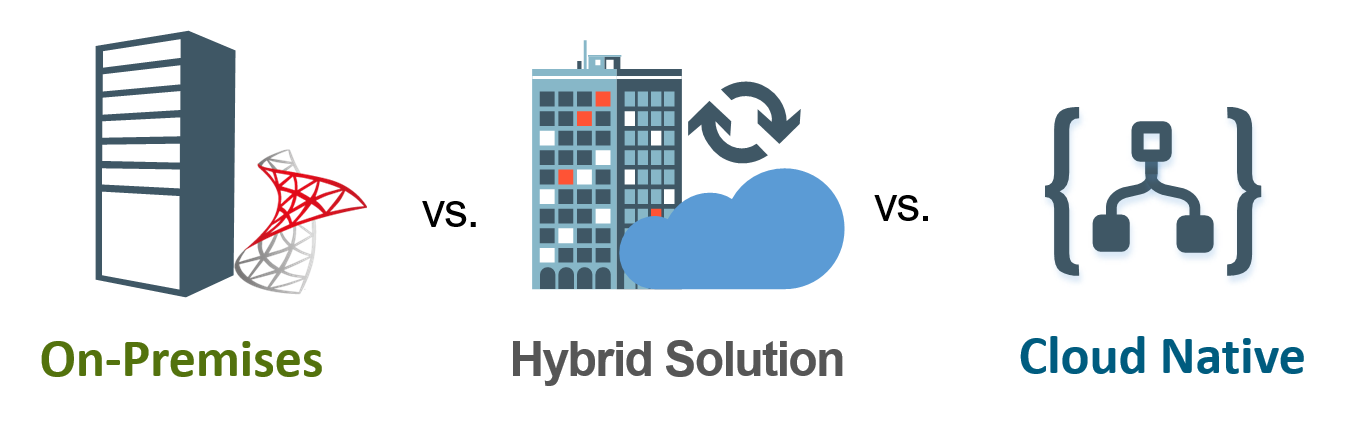 Choosing the suitable integration model will generally depend on the organization’s overarching cloud adoption strategy, it will also depend on whether the majority of integrated systems lie on-premises, in the cloud, or spread across.
Choosing the suitable integration model will generally depend on the organization’s overarching cloud adoption strategy, it will also depend on whether the majority of integrated systems lie on-premises, in the cloud, or spread across.
Forces shaping the integration landscape
Let’s imagine the cloud adoption progress as an imaginary spectrum; starting with the on-premises model at the far left, all the way to the cloud native model at the far right, and in-between is the hybrid integration model with different levels of cloud adoption progress.

Generally, the organization’s cloud adoption decision is influenced by two opposing forces: blocking factors and modernization.
Blocking factors are limiting organizations from moving partially or completely to the cloud, these factors could be due to compliance regulations, on-premises solution complexity, budget constraints, just to name a few.
Modernization is the allure of reaping the benefits that the cloud platform brings, such as productivity gains, cost savings, global reach, the availability of powerful service offerings.
Hybrid Integration: The Old meets the New
Hybrid Integrations provides a compromise, where the core on-premises investments are still maintained while its features are being extended by the new cloud service capabilities.
Today, the IT landscape of many organizations lies within the Hybrid integration section of the spectrum with various levels of cloud adoption progress; whether this progress has been a part of a carefully planned and executed strategy or it was a gradual, ad-hoc progress driven by necessity.
Azure Hybrid Integration Techniques
Implementing hybrid integration solution in Azure could be achieved with multiple techniques, in this section I will summarize three main techniques, I will also show possible variations in Azure integration offerings and the on-premises downstream systems.
1. Site-to-Site (S2S) VPN
This technique leverages a S2S VPN tunnel connecting Azure to the organization’s on-premises network through public internet using a VPN Device at the on-premises side and Virtual Network (VNET) VPN gateway on Azure, thus creating a secure VPN tunnel that encrypts traffic between the Azure VNET and on-premises network.
This is a familiar technique to organizations that already have S2S VPN connecting remote locations such as offices around the globe.
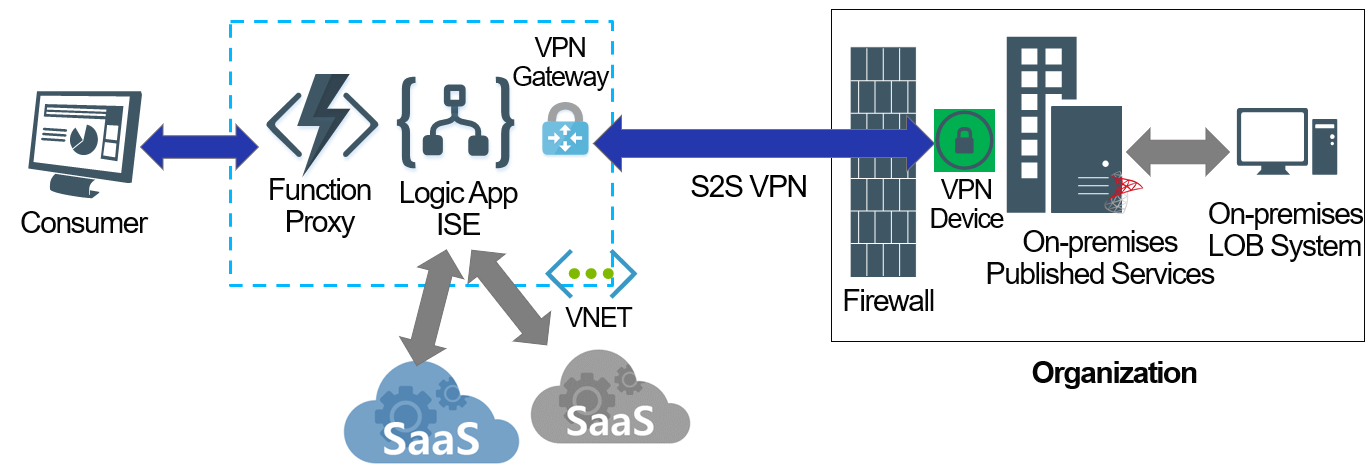
It is worth mentioning that in order for an Azure service to leverage the VPN connectivity, the service will need to support VNET integration capability, this feature is usually included in the premium plans of Azure services that support this capability.
For instance, using the Logic Apps integration service environment (ISE), a premium tier, is required in order for the hosted logic apps to have VNET access capability which in turn allows it access to on-premise systems through the S2S VPN tunnel.
2. Direct Integration
In case the on-premises system already provides secured web services that are published over the public internet using industry-standard, supported communication protocols, integrations can be accomplished directly from Azure services.
Certainly, this is assuming that proper security measures were taken on the firewall, network, transport, and message levels, where necessary.
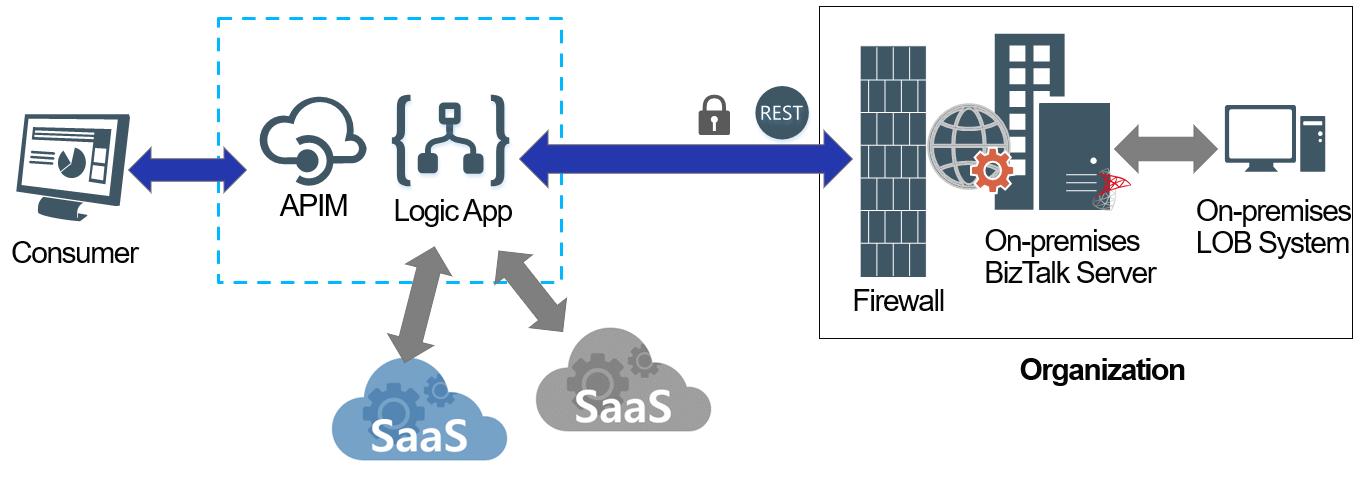
For instance, Logic Apps can leverage the standard HTTP connectors with the required HTTP headers, and authentication scheme to connect to a secured on-premises REST endpoint published on public internet. On-premises, it may be required to create a dedicated service principal in the local identity server and may be apply local firewall configurations to allow traffic coming from the Logic Apps IP addresses.
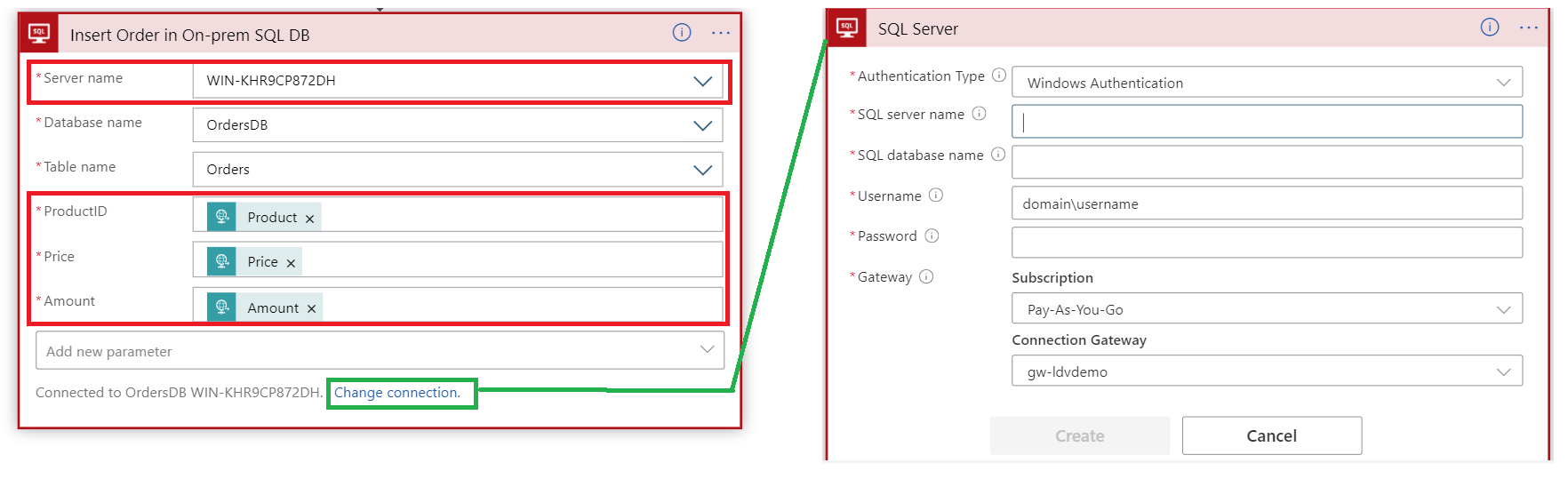
3. Data Gateway
Another technique is to leverage On-premises data gateway which provides a secure connectivity between supported on-premises data sources and selected Azure cloud services that support it.
This approach leverages a gateway cloud service on Azure and a light-weight service agent running on-premises. An initial installation and setup will be required to register the on-premises gateway agent with Azure gateway cloud service.

This technique creates a secured bridge that facilitates integrations between the supported Azure services and on-premises data sources without introducing intrusive changes to the organization’s firewall or the on-premises data source security scheme.
For instance, Logic Apps can use its on-premises connectors via the data gateway, thus leveraging the rich UI interface provided by logic apps when connecting to on-premises data sources, this simplifies connectivity, service discovery, and payload inflation, all of which boosts productivity.

On-premises data gateway makes it possible to integrate with the on-premises data sources such as the file-system and SQL Server using native Windows Authentication credentials; this is a very powerful feature to quickly and securely integrate with on-premises data sources without the need for any additional mediating layers or the need for changing the existing security schemes for these data sources.
It is worth noting that stored credentials are encrypted on Azure and they are only decrypted by the on-premises agent when connecting to the on-premises data sources.
Final Thoughts
In this article, I talked about the evolution in Microsoft integration landscape with the advent of Azure service offerings, and how organizations were faced with new integration models.
I also summarized three main techniques to implement hybrid integration model in Azure with the support of dedicated Azure services and technologies.
For many organizations, the integration landscape is within the hybrid area, with the modernization promise and the blocking factors as the two opposing forces influencing cloud adoption decision and progress.

Finally, there is no absolute right or wrong model, organizations’ integration solutions will possibly evolve during its lifetime among these models at different stages. The progress level of cloud adoption will generally depend on the influence of the two opposing forces in shaping the organization’s decision at each stage, hopefully along a strategic direction.